No bolting on. Baked in from the get go
Secure by design vs fixing in production.
50% of software vulnerabilities are flaws at the design stage. It is 100x more expensive to fix these flaws in production. IriusRisk is here to solve that...
From the ground up.
Just add code.
How threat modeling brings advantages across the SDLC
Speed and efficiency
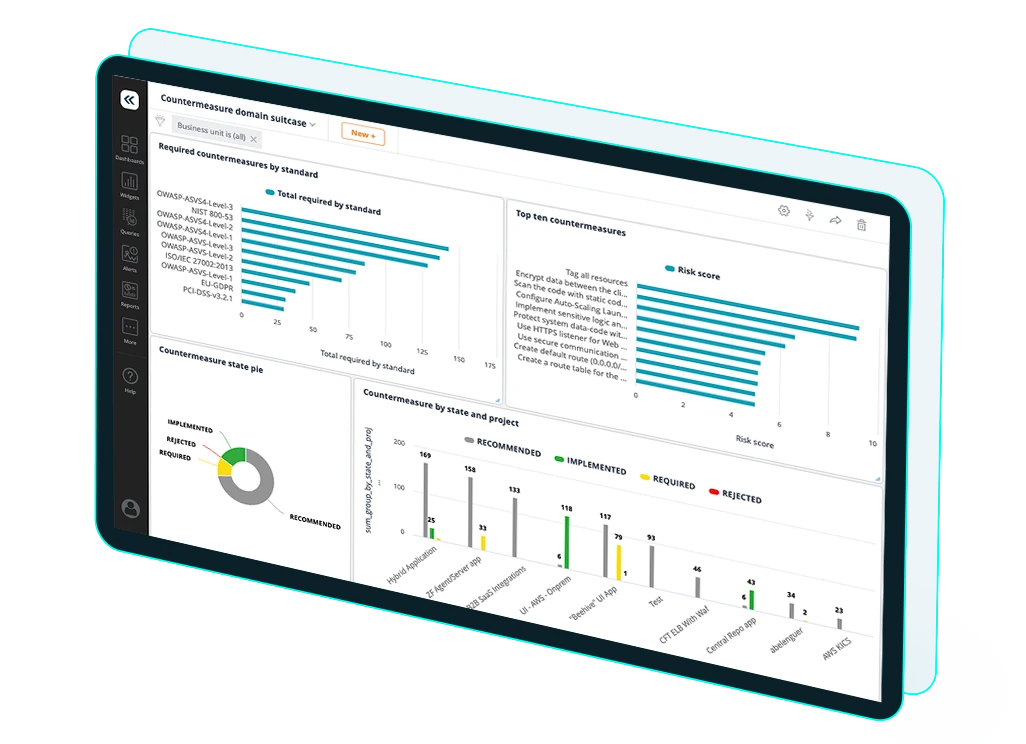
Decide what actions to take based upon the threat modeling findings.
Smarter development
Identify potential flaws - even before code is written.
Automate further
Integrate into existing CI/CD tools, issue trackers and scanning software.
Secure by design
Increased confidence in deployment and reliability of code.
Pen test only what matters
We provide the plan for focused and efficient testing.






